HashiCorp Boundary: A Game Changing Infrastructure Access Solution
Last week, HashiCorp announced the release of Boundary, a game-changing infrastructure access solution aimed at helping developers, operators, and security teams maintain access controls for on-premises and cloud infrastructure.
Here at NextLink Labs, we couldn't be more excited about this security-minded offering. Being a company located at the heart between DevOps and Security, we often encounter problems that, up until the release of Boundary, required much more complicated tools and processes to solve.
Boundary is a tool built to make it simple to grant and maintain access to infrastructure. In true HashiCorp fashion, Boundary accomplishes this in a way that can target any sort of infrastructure, including all the major cloud providers, Kubernetes, and on premise infrastructure.
Specifically, this tool enables access from a public user to many types of hosts and services located in a private network, and integrates with many existing Identity Providers such as Okta, Active Directory Federation Services, Active Directory, and more.
The Challenge: Connecting Public Users to Private Resources Simply
Most modern systems have resources located on a private network for which are going to need to be accessed by end users on a public network. Examples are vast but a few simple ones are databases, web service hosts, kubernetes nodes, or something similar.
In order to grant users outside the network access to these resources, three things need to happen:
- A VPN or Bastion host needs set up as a gateway to bridge connections onto the resources
- The connection must be restricted via firewall rules or similar so when you give a user access to the VPN or Bastion host they only have access to the resources they need and not the entire network
- Individual credentials for each resource must be shared (DB credentials, ssh keys, etc)
Doing things this way brings up a few issues with their own challenges that require solving:
Issues with Onboarding and Offboarding Users
Users must be granted a series of credentials and keys at different layers of the system. Not only is this difficult in and of itself, but when you throw in best practices around key rotations, static credentials, and how you handle dynamic infrastructure like auto scaling groups and kubernetes services, it can quickly become too much to handle.
Problematic, Unclear Visibility into Connections
We consider it a security best practice (and oftentimes a compliance requirement) to have visibility into what users and systems are connected where. This sort of access control record needs to be available in logs for security personnel to review.
Difficult Integration and Tooling
Users may need managed in multiple Identity Providers and other systems. Power users who are attempting to use command line tools or other tooling may find it difficult to work within the constraints of the VPN or bastion host setup
Boundary solves these issues by abstracting away much of the complexity and changing the way you think about access to system resources.
How Boundary Makes it Work
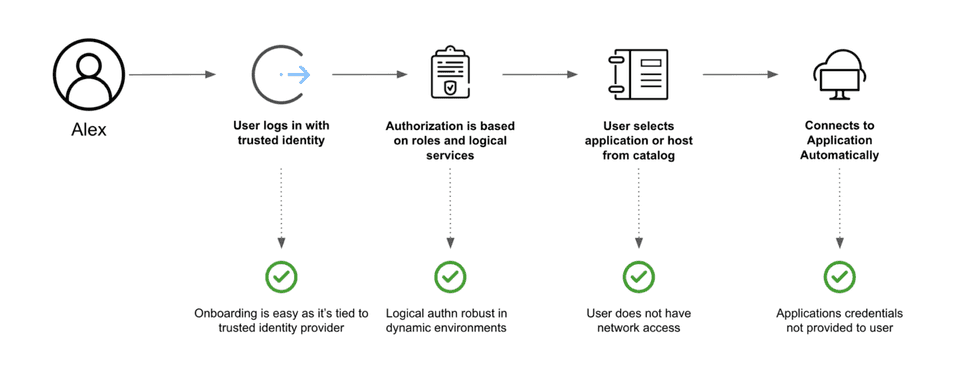
As mentioned previously, HashiCorp Boundary was built to make it easy to grant and maintain access to infrastructure.
So what does that look like in practice?
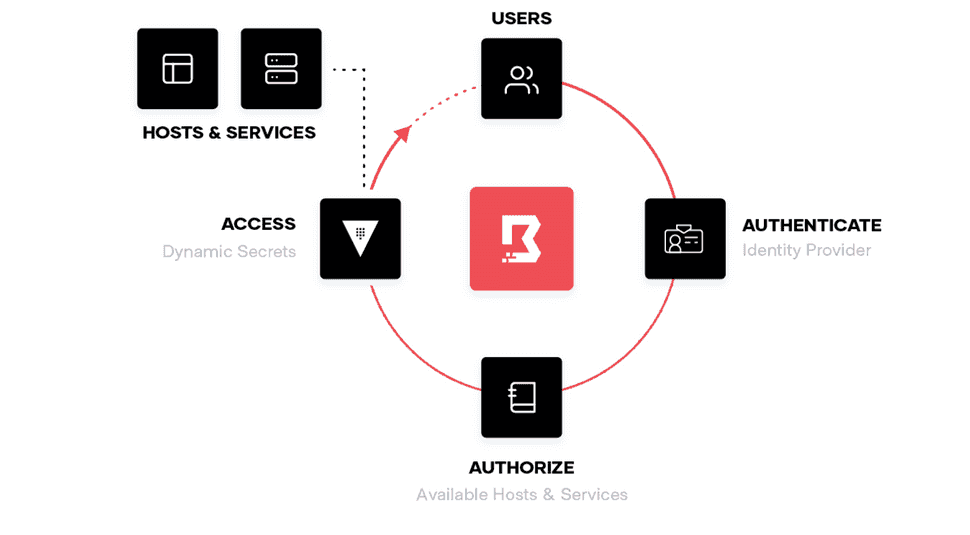
In initiating a boundary connection, 3 things happen:
-
Authentication: Boundary replaces individual Ssh keys and credentials with SSO via OpenID Connect. So the first step is to authenticate a user against an existing IDP (Identity Provider) such as Okta or ADFS.
-
Authorization: Boundary checks its list of role based access controls to see if the authenticated user has access to the desired resource.
-
Connection: Boundary initiates a connection to this resource. It does so via a client side agent that exposes this connection via localhost. Allowing a seamless experience with existing tools as you can work as if the connection is just a localhost connection. For many types of tools, this can also handle the credentials aspect of using a service so your end user never needs to be shared static credentials that may leak or be exposed.
To the end user, they are able to use boundary in several different ways:
- CLI
- SDK
- REST API
- User Interface
- Desktop application (coming soon!)
With options for using Boundary that should appeal to both power users and less technical users, Boundary should provide a great user experience that will not only make your operations and security folks happy, but also provide tremendous value to end users.
The Key Advantages to Boundary
We think HashiCorp Boundary is a gamechanger for many organizations.
It is truly a tool set up for the future as it’s architecture supports modern cloud architectures.
HashiCorp says that in solving this common problem their users were experiencing (access to resources in a private network from a public network), they fundamentally changed how they think about solving the problem.
Boundary has many advantages over other ways of handling the issue:
- Access rules can be setup and handled as code via their Terraform provider (provides all the other benefits of Infrastructure as Code)
- Policy is thought of as “which set of users needs access to which set of services” as opposed to IP based access control - which is brittle, especially in today’s increasingly ephemeral environments
- Access to Session Visibility: Security Administrators are able to monitor and manage privileged sessions and export the session logs into analytics tooling
- Promotes a zero-trust network security model as it does not trust the private network and does not give unnecessary access to the private network
- Makes onboarding and offboarding users a breeze. You only need to add or remove users to your Identity Provider. You don’t need to set up VPN or SSH access. You don’t need to grant individual user credentials
Wrap up
In summary, we believe HashiCorp Boundary to be an excellent addition to many companies' toolchains. It does an excellent job of automating the setup and access of resources, identities, and access controls as code with Boundary’s Terraform Provider, REST API, CLI, and SDK. We think Boundary solves a common problem most organizations have in a way that enables simplicity for its users and operators while keeping security top of mind.
If you think your organization could benefit from a tool like HashiCorp Boundary, please reach out to us here at NextLink Labs and we are happy to help discuss how we can help.